Nikon Z6 III’s C2PA Functionality Has a Significant Security Vulnerability
![]()
Nikon’s first major firmware update for the Nikon Z6 III arrived last week, adding bird-detect autofocus, Auto Capture, and C2PA Content Credentials.
While firmware 2.00 brings many great features to the Z6 III, its C2PA implementation includes a significant oversight. It is possible to combine multiple RAW images captured by Nikon Z6 III cameras, including one that is not C2PA-enabled, and deliver a photo that passes authentication checks. The Z6 III can, in at least one situation, sign a photo that shouldn’t be approved.
Nikon notes the C2PA functionality, which has been in development for a while and is part of the new Nikon Authenticity Service, is technically in beta. Nonetheless, beta or not, the C2PA functionality is still active and available to the public.
Nikon tells PetaPixel that “An investigation is currently ongoing.” Given the company’s track record of quickly reacting to any issues with firmware, and the importance of the Z6 III’s C2PA functionality for some professional photographers, PetaPixel expects the company to move quickly on the matter.
The C2PA issue was discovered by Adam Horshack, whose other work was recently discussed in a detailed report concerning the Panasonic Lumix S1 II’s shockingly good dynamic range performance. Horshack explained his Z6 III C2PA findings over on DPReview‘s forums, and his complete post is suggested reading.
![Screenshot of camera menu instructions. Step 6 shows how to select Overlay shooting, with a highlighted Overlay shooting [ON] option. Step 7 explains choosing a RAW image for first exposure, with a menu showing photo thumbnails.](https://petapixel.com/assets/uploads/2025/09/nikon-z6-iii-user-manual-multiple-exposure-800x454.jpg)
The quick-hits version of Horshack’s findings is that the Z6 III’s Multiple Exposure mode is the culprit of the C2PA circumvention.
Horshack has access to two Nikon Z6 III cameras, and he enabled C2PA functionality on only one of them. Using the Z6 III without C2PA, which he describes as the “imposter” camera in his testing, he captured a RAW photo of a graphic he created in Photoshop that reads, “Hacked by Horshack!”

Horshack removed the memory card from this camera and put it inside the C2PA-enabled Z6 III body. He then used the camera’s Multiple Exposure mode, set it to capture two shots with “Overlay Shooting” enabled, put “Overlay Mode’ on Light, and then had the camera select the first exposure (RAW) on the memory card as one of the two frames to be used in creating the final Multiple Exposure image. The photo that Horshack captured using the C2PA-enabled Z6 III had the lens cap on, so it was just a black frame.
As shown below, the image is signed by the Z6 III’s C2PA feature and passes the Content Authenticity Initiative’s (CAI) online verification tool. This is not good because the meaningful part of the image, namely the entire image itself, was captured using a camera without content authenticity enabled. It is possible to capture a photo of just about anything, including AI-generated images, using this workaround and have them pass CAI checks and show up as a genuine, authentic photo captured by a verified Nikon Z6 III camera. The Z6 III can currently be used to capture and spread images with what are effectively false signatures.
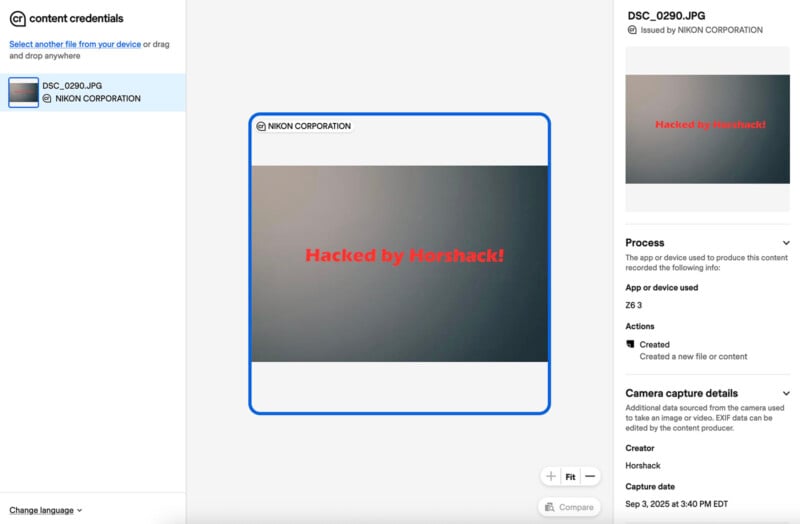
Horshack says this experiment “demonstrates the dangers of ‘soft targets’ in a C2PA-enabled system.” As he rightly notes, he did not circumvent the actual cryptographic mechanism of the Z6 III, but he did render it essentially meaningless.
Adding in our two cents, an obvious solution to a problem like this would be preventing the Z6 III’s Multiple Exposure mode from accepting input images captured without C2PA protection. So in this case, the Z6 III should not have allowed an unsigned image to be used in the Multiple Exposure on a C2PA-enabled camera. While it may not necessarily be straightforward to change how the Multiple Exposure mode works on the Z6 III, that is one potential solution.
Another possible solution, and one Horshack notes, would be to prevent the Z6 III from signing an image captured using the Multiple Exposure mode altogether, which seems like a perfectly reasonable option that would not add significant limitations to the utility of the Z6 III’s C2PA functionality.
Nikon will also have to develop a solution that not only fixes the security issue but also prevents it from causing future harm to users who choose not to update their Z6 III again. Given that the C2PA functionality connects with Nikon Imaging Cloud, it will hopefully be possible to entirely kill the ability to sign images on cameras that don’t have a specific firmware version installed.
Image credits: Header photo created using an asset licensed via Depositphotos. Additional images and research provided by Adam Horshack.