New Russian-Linked Android Spyware Takes Control of Camera and Mics
![]()
A new Android spyware has surfaced that disguises itself as a system component and can access a variety of smartphone functions including the microphone and camera to secretly record the user.
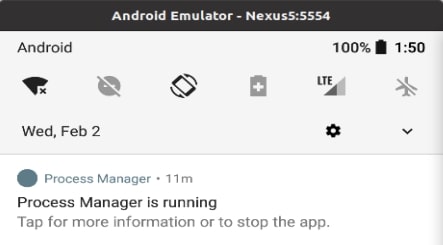
Researchers from Lab52 discovered the malicious APK spyware that is named “Process Manager” and can upload information gleaned from devices it is installed on to a third party. It’s still not clear how the spyware is distributed but once installed, it attempts to hide by using a gear-shaped icon and posing as a legitimate Android system component, Bleeping Computer reports.

Once the application is run, a warning will appear that asks the user to grant permission to the application, which includes screen unlock attempts, locking the screen, setting the device global proxy, setting the screen lock password expiration, setting storage encryption, and disabling cameras. Lab52 found a large number of permissions that it requests including:
- GPS data including phone location
- Network status
- WiFi information
- Full access to the camera for both photo and video capture
- Audio modifications
- Access to call logs
- Access to contact list
- The ability to read external storage
- The ability to write to a memory card
- SMS access on the SIM card
- Access to the audio recorder
- Permission to send SMS messages
- Permission to prevent a decice from locking or hibernating
After it has been selected and runs, the icon disappears and the malicious application continues to run in the background. Oddly, it shows as active in the notification bar. Obviously, this long list of permission would be a massive privacy breach for the user, but the existence of the permanent notification is confusing, as spyware like this would benefit from being completely hidden from the user.
Whatever the case, the information that is collected from infected devices is sent in the JSON format to a command and control server with an IP address in Russia. Bleeping Computer says that the way this spyware works is similar to methods used by Russian state-supported hacking group Turla, but stopped short of making a definitive link in this case. If Turla is involved, the app may be propagating through a variety of social engineering techniques or phishing.
Lab52 found a link to a Google Play store listing called “Roz Dhan: Earn Wallet cash,” which uses a referral system to earn money. The attacker seems to install the app on the target device and make a profit.
Android users are encouraged to look at app permissions they have granted and check for the “Process Manager” application and revoke access if it appears.
Image credits: Header photo licensed via Depositphotos.