PSA: Canon DSLRs are Vulnerable to Ransomware, Update Yours Now
Canon has issued an official security advisory for its WiFi-connected DSLRs after a security company showed that they could remotely hack into and install ransomware on a Canon 80D. The findings, which were shared with Canon ahead of the public reveal, have left Canon scrambling to patch a serious security flaw.
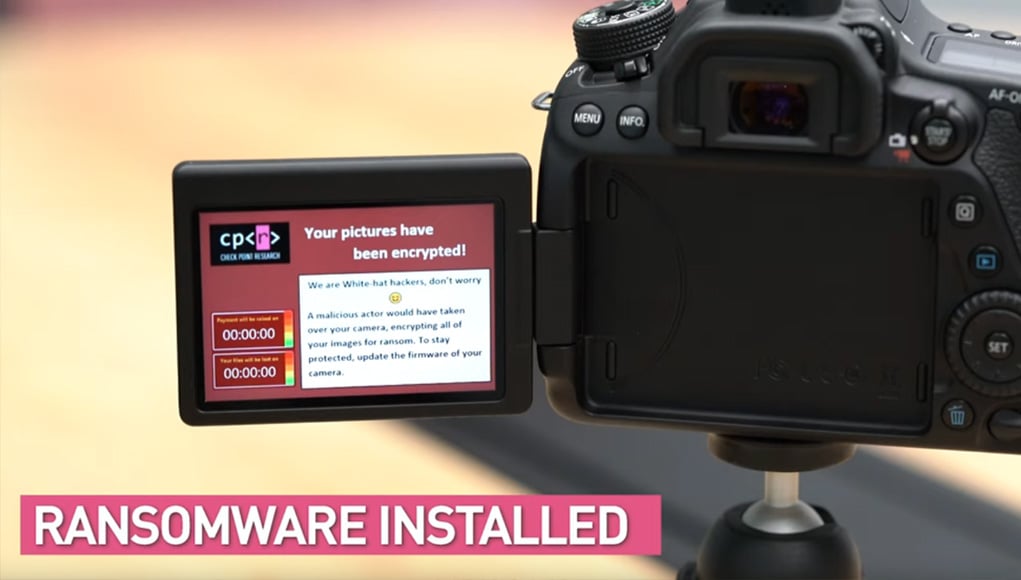
The critical flaw in Canon’s Picture Transfer Protocol was reveled by Security Company Check Point Research during Hacking Conference DEF CON 2019. As you can see in the demo video above, the company was able to take full control of a Canon 80D using either a USB or WiFi connection. Once they had control, they were able to install “ransomware,” encrypting all of the photos on the SD card and holding them hostage until and unless the victim pays a sum of money (usually in cryptocurrency) to receive the encryption key and unscramble their images.
As Check Point explains in their in-depth article detailing the flaws, “such an [infection] will allow attackers to do whatever they want with the camera, and infecting it with Ransomware is only one of many options.”
The hack was built using the extensive information already available through Magic Lantern, making Canon the the most convenient target for Hackers, but it’s entirely possible that the same security vulnerabilities are present in other manufacturers’ wireless transfer protocols. “Based on our results,” says Check Point, “we believe that similar vulnerabilities can be found in the PTP implementations of other vendors as well.”
The details of the vulnerability and how it was exploited are complicated, and you can read all about it on Check Point Research’s website. Fortunately, they’re not a malicious hacker, so they disclosed their findings to Canon on March 31st, long before making the findings public. Since then, they’ve worked together with Canon to patch the vulnerabilities that were found, which is why these findings were released alongside an official Security Advisory from Canon itself.
As Canon explains, there have been no reported cases of this vulnerability actually being exploited to install ransomware IRL, but now that the info is out there, the company is working as quickly as possible to patch affected DSLRs. Canon already quietly released a firmware patch for the 80D on August 6th, which users should download and install right away. But until all of its WiFi connected DSLRs have been patched, Canon suggests that users:
- Ensure the suitability of security-related settings of the devices connected to the camera, such as the PC, mobile device, and router being used.
- Do not connect the camera to a PC or mobile device that is being used in an unsecure network, such as in a free Wi-Fi environment.
- Do not connect the camera to a PC or mobile device that is potentially exposed to virus infections.
- Disable the camera’s network functions when they are not being used.
- Download the official firmware from Canon’s website when performing a camera firmware update.
To learn more about this vulnerability, head over to the Check Point Research website. And if you own a WiFi-connected Canon DSLR, be sure to check Canon’s Support website religiously until an appropriate firmware update has been released and installed.
(via Hacker News)