Sony’s Camera Firmware Updater is a Major Security Risk, Expert Warns
![]()
If you use Sony cameras, here’s something you should be aware of: a computer security expert is warning that Sony’s camera firmware update process has serious security risks that could put your computer and data in danger.
“That means it can install things like a keyboard sniffer, transmitting everything you type to some hacker in Belarus, so to speak,” Chambers says. “Thus all your accounts, all your money, your identity, etc is placed at risk.”
Apple has been tightening up security in macOS, and Sony warned late last year that the latest security system in macOS 10.13 High Sierra may cause Sony’s firmware updater for cameras such as the a7R III to not work.
![]()
“Approaches that in essence require operating system kernel access are incredibly badly designed given the security risks,” Chambers says.
In January 2018, Sony unveiled its solution to the problem of its updater not working in High Sierra… but instead of responding to Apple’s stricter security with a safer firmware update system, Sony posted a tutorial teaching camera owners how to install the kernel extension and grant permissions in High Sierra.
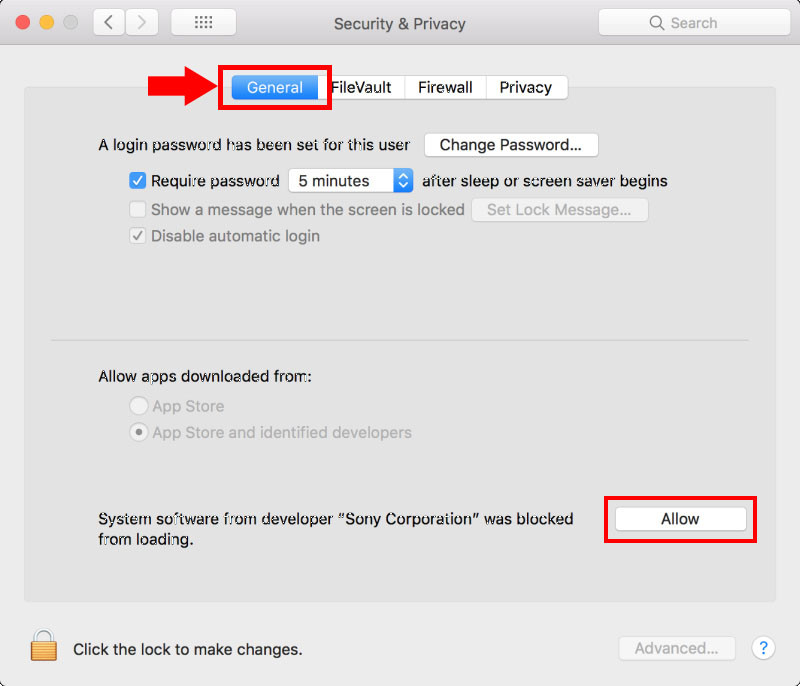
“The Sony kernel extension is (quite appropriately) blocked by macOS because it is a very very bad idea,” Chambers says. “In this day and age, requiring a kernel extension to install a firmware update for a camera shows gross ignorance of the security risks and in my view, is incompetence.”
Here’s what Chambers tells PetaPixel about how things currently stand:
The current status of the Sony firmware updater is unacceptable because it requires the user to assume that Sony software is free of malware. That the software is signed only guarantees that something was signed by Sony, not that it is free of any infection (infection could have occurred prior to signing).
If Sony software is ever compromised (including at the source code level!), that malware would have unfettered root/kernel access to the system until the system were wiped out (assuming such an infection did not overwrite firmware in various places, in that case the machine becomes dumpster material).
Since Sony Pictures with highly valuble intellectual property was hacked a few years ago (taking the company down for weeks), no user should ever trust what could become a “root kit” firmware updater for hackers.
The ONLY acceptable solution is an in-camera firmware updater. Even that is not risk free (the download process), but it does not directly expose the computer at the kernel level, or even admin level.
That there is risk is self-evident in Sony’s need to bypass what Apple now considers core security prohibitions. Indeed, the Sony kernel extension cannot just be installed but requires explicit enabling by the user after installation, that is, on the new iMac Pro with its secure enclave and much more locked down boot security.
If you’d rather not trust Sony and place the security of your computer in the company’s hands, Chambers recommends that you install the firmware update using a temporary virtual machine and then delete the VM afterward.
PetaPixel and Chambers have both reached out to Sony for comment on this security issue, but the company has yet to respond to our multiple requests.